Software Engineering
Performance. Security. Reliability. Scale.

Innovate, Inspire, Enjoy!
Programmers who do not accept the Dao always lack time and space for their programs. Programmers who accept the Dao always have enough time and space to achieve their goals.
Could it have been otherwise?
Performance. Security. Reliability. Scale.
Rapid Validation. Feasibility. Demo-Ready Prototype.
Native Interfaces. Predictable Performance. Deep Visibility.
Drivers. Minifilters. Safe Rollout. Diagnostics.
Binaries. Firmware. Protocols. Forensics.
Ultra Low Latency. Deterministic Execution. Tail Latency.
Threat Modeling. Code Review. Exploit Paths. Retesting.
Architecture. Performance. Scalability. Security.
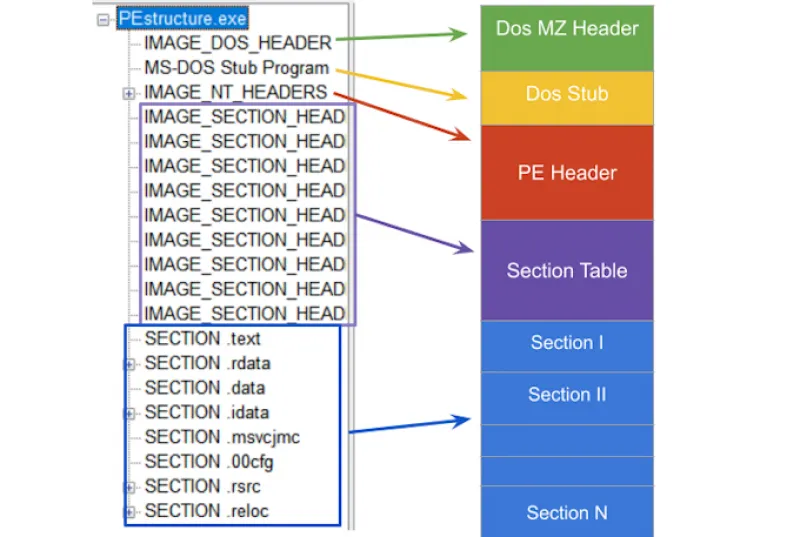
Hello dear friends! In this article, we’ll cover the basics of the PE format and build our own parser from scratch. It will be useful for those working in cybersecurity with system software, antivirus solutions, and protection systems.

Friends, hello everyone! In this article, we will talk about such an important part of every antivirus engine as the hashing module. We will talk about data verification, blacklisting and whitelisting, finding out how similar or different data is, and touching on the topic of fuzzy hashing algorithms. Get comfortable in your chairs!
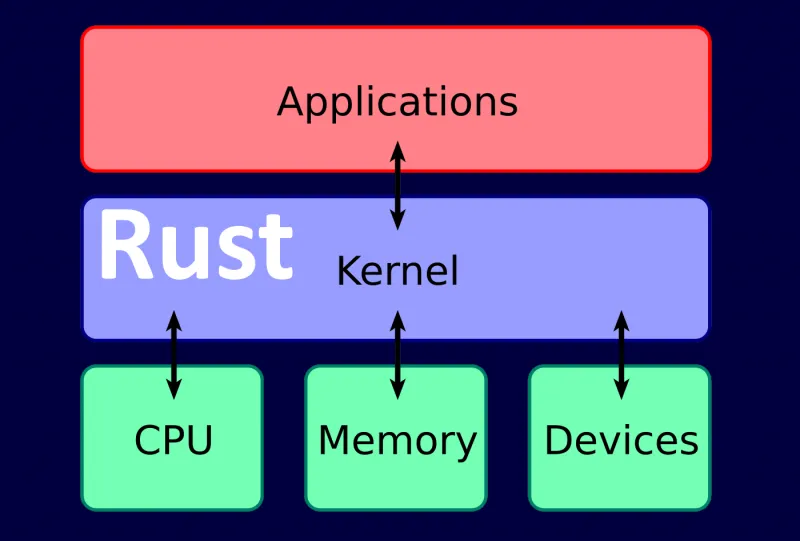
Build your first Windows kernel driver in Rust with a practical, step by step setup that covers WDK, Windows SDK, nightly toolchain, linker flags, and a clean no_std driver entry using DbgPrint. This guide walks through compiling a Rust .sys driver, enabling Windows test signing mode, signing the driver, and validating output with Sysinternals DebugView on Windows 10 or Windows 11.
Hello friends! In this article, we will analyze an executable file that repeatedly found itself on the work network of one of our clients and created problems for the client. The client asked to reverse-engineer the threat, conduct a security audit and provide a solution, which we did. We are always glad to cooperate in the field of cyber security, reverse engineering and security audit!